Two-Factor Authentication (2FA)
Add an extra layer of security with two-factor authentication in your mobile app.
TurboStarter uses Better Auth's 2FA plugin to provide multi-factor authentication (MFA) capabilities in your mobile app. Two-factor authentication adds an extra layer of security by requiring users to provide a second form of verification alongside their password.
Available methods
TurboStarter supports multiple 2FA verification methods through Better Auth:
- TOTP (Time-based One-Time Password) - codes generated by authenticator apps
- OTP (One-Time Password) - codes sent via email or SMS
- Backup codes - single-use recovery codes for account recovery
You can use any TOTP-compatible authenticator app, such as:
Enabling 2FA
Enable in settings
Users enable two-factor authentication in their account security settings within the mobile app.
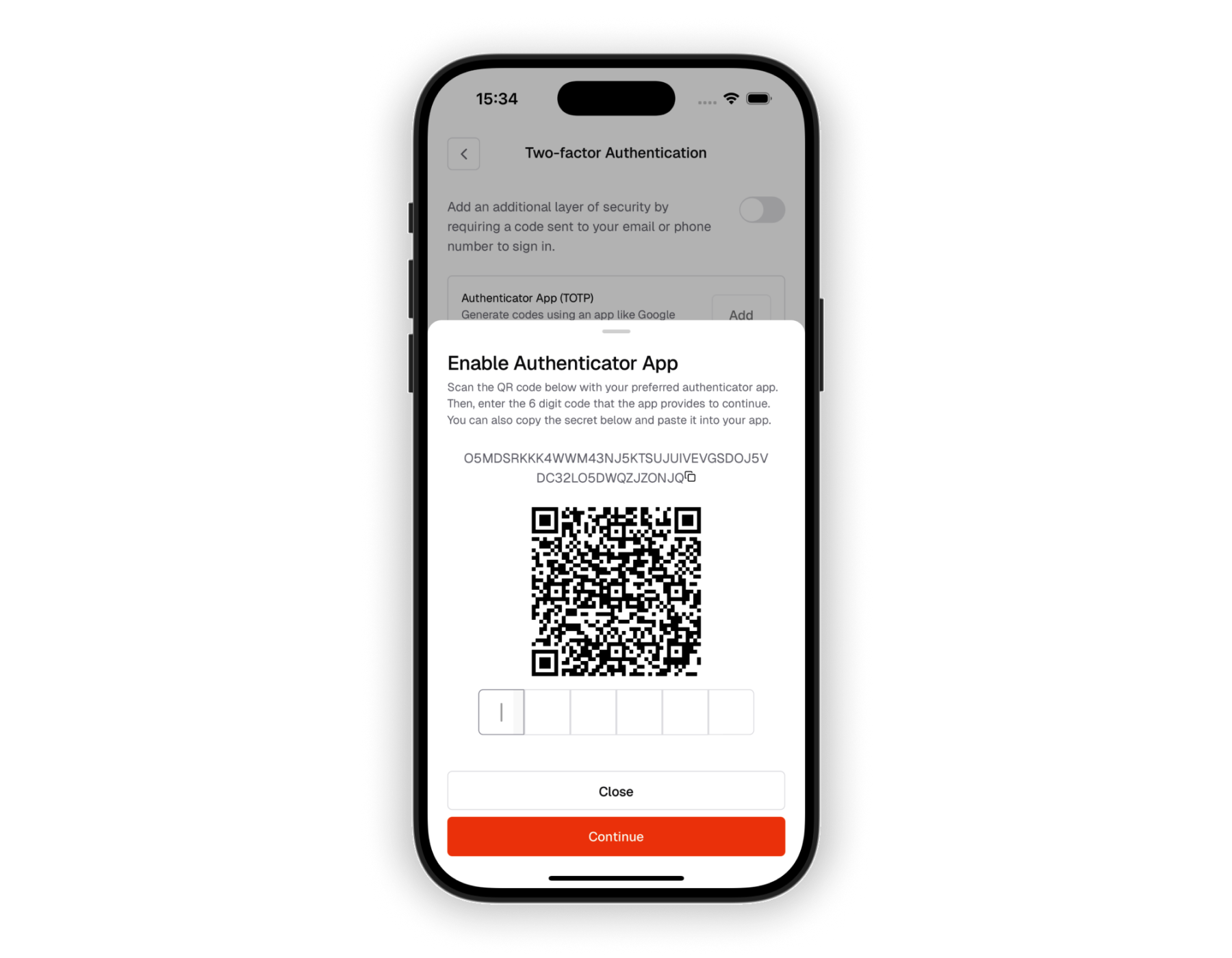
Setup authenticator
A QR code is displayed in the mobile app for users to scan with their authenticator app. Users can also manually enter the setup key if needed.
Verify setup
Users enter a verification code from their authenticator to confirm setup directly in the mobile app.
Backup codes
Users receive single-use backup codes for account recovery, which can be saved or shared from the mobile app.
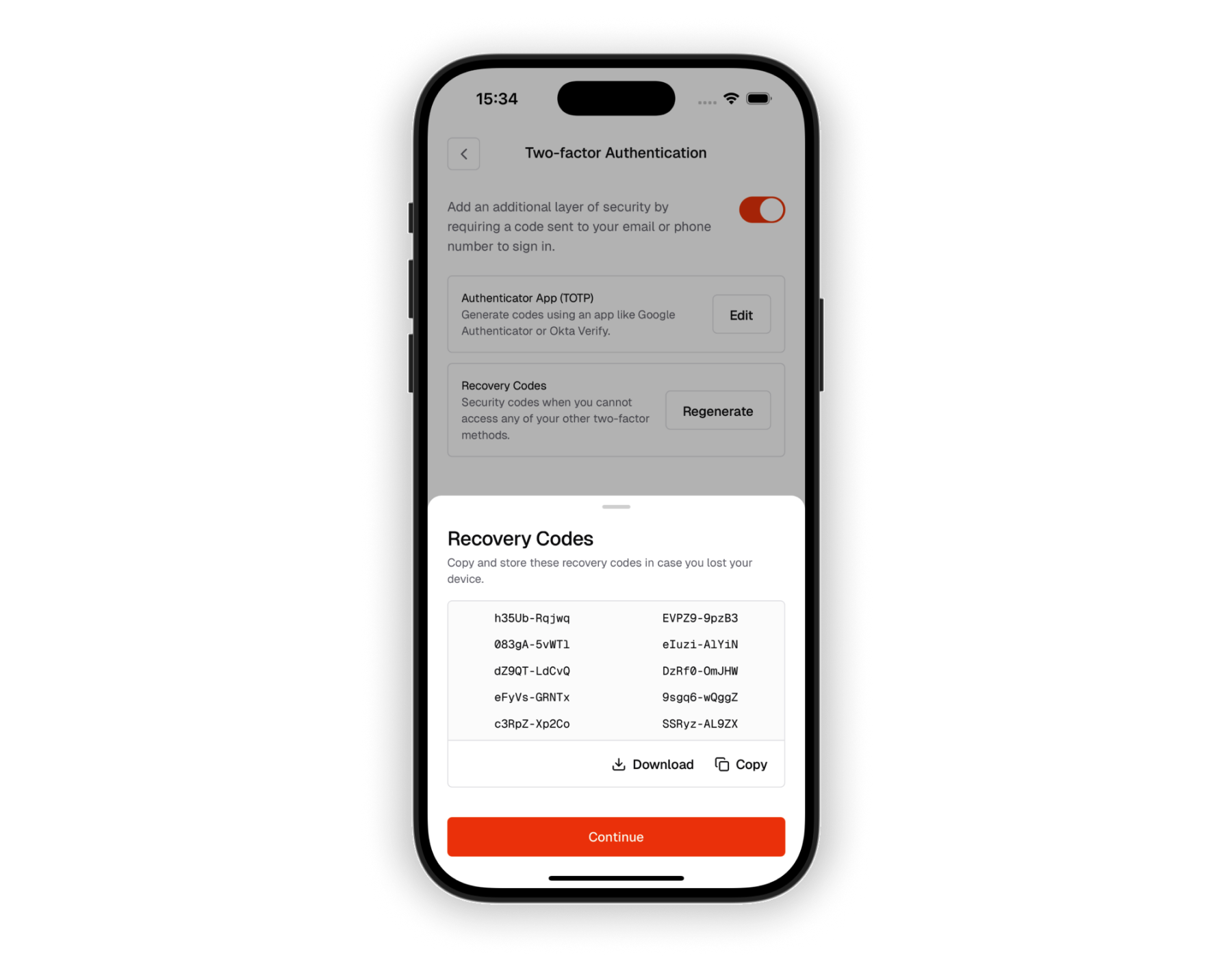
Recovery codes are essential for account recovery if users lose access to their authenticator device. Make sure to educate users about safely storing their backup codes, and consider providing options to save them to the device or share them securely.
Using 2FA
Sign in normally
Users enter their email and password or use other authentication methods (biometric, social login) as usual in the mobile app.
2FA prompt
After successful password verification, users are prompted for their 2FA code in a native mobile interface.
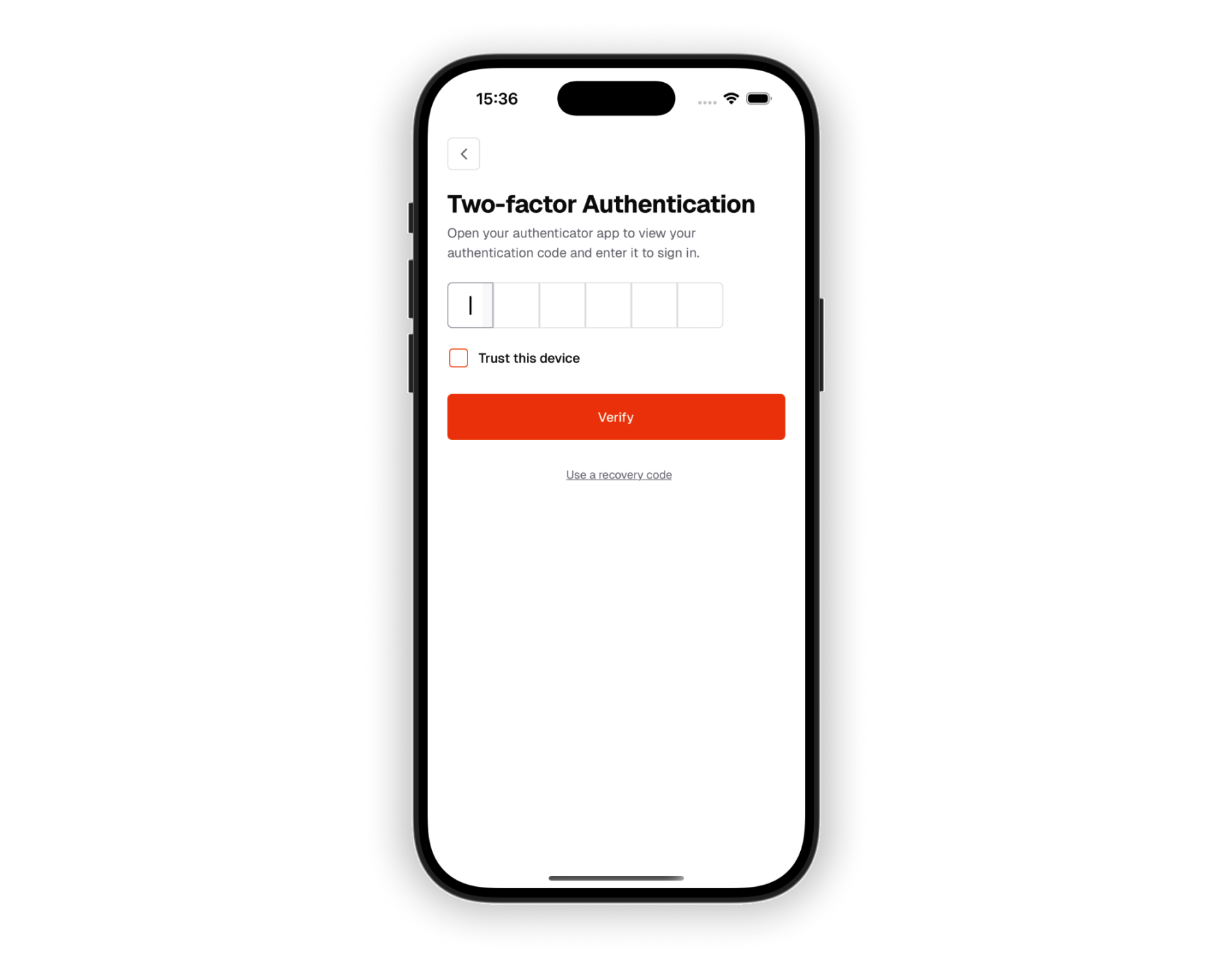
Enter verification code
Users input the 6-digit code from their authenticator app using the mobile keyboard.
Access granted
Upon successful verification, users gain access to their account and are navigated to the main app screen.
Trusted devices
Users can mark their mobile device as trusted during 2FA verification. Trusted devices won't require 2FA verification for 60 days, providing a balance between security and convenience. This is particularly useful for personal mobile devices.
Mobile-specific considerations
Biometric integration
On mobile devices, 2FA can be enhanced with biometric authentication (fingerprint, face recognition) for added security and convenience.
App switching
The mobile app should handle switching between your app and authenticator apps seamlessly, maintaining the authentication state when users return.
Offline support
Consider implementing offline backup code verification for scenarios where users may have limited connectivity.
Push notifications
For OTP delivery via SMS or email, ensure your app handles incoming notifications gracefully during the authentication flow.
Configuration
2FA is configured through Better Auth's plugin system. The plugin handles:
- Secure secret generation and storage
- QR code generation for authenticator setup
- TOTP code validation
- Backup code generation and management
- Trusted device management
- Mobile-specific session handling
For detailed implementation instructions, refer to the Better Auth 2FA documentation.
How is this guide?
Last updated on